iApps Development Blog

Is This For Real?
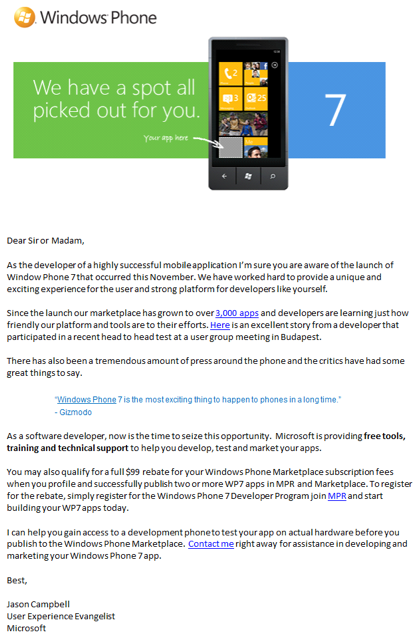
I normally cover suspicious email messages over at my spamwars.com site, but because the likely recipients to be taken in by the above email message are mobile developers, I’m talking about it here.
Several huge red flags waved vigorously when I first saw this message. To name the top ones:
-
✦The To: field had an address I have never used to register anything with Microsoft.
-
✦The message body is addressed to “Dear Sir or Madam”.
-
✦The grammar (beginning with the very first sentence) is atrocious.
-
✦The message text is actually an image file (and a .png at that). Those blue underscores are not separate links.
-
✦The image in the message’s HTML is surrounded by a hyperlink tag that goes to a bing.com URL with many parameters.
But (and it’s a big but), according to the message header, it did, indeed, come to my server directly from a mail server in an IP block owned by Microsoft.
What you also don’t see is that the message came with a .wmz file, which is a compressed Windows Media Player skin file (under normal usage). The body of the message (that is, the body containing the image above) was generated with Microsoft word (oh, all that horrible XML markup...blech), and it’s possible that if the message is opened in an Office-compatible reader, the .wmz file would load. I ran the .wmz file through VirusTotal, and it found no matching signatures. There was a .wmz exploit in the Windows wild a few years ago, although it has long been patched.
Assuming that most recipients of this message to be tantalized by its content would be Mac users, I don’t believe the .wmz payload, even if nasty, is the primary goal of the sender. My attention is focused on the bing.com URL. Not being a Bing specialist, I don’t know what all the URL parameters signify. The field names for the visualsearch URL are: g, ve, qpvt, and FORM. Unfortunately I don’t have the time today to track down what these parameters mean. The goal of the sender, however, is to trick the recipient into clicking this link — made especially easy because the whole freaking email image is the active link. Thus, my suspicions lead me to believe this is a search engine optimization poisoning ploy.
The sourcing of the message from a Microsoft IP block is still a head-scratcher, unless someone’s PC up there has been compromised and has so far been undetected.
As is my usual response to any attempt to trick, I won’t play the game and click the link. I hope you’ll follow suit if you are confronted with this type of gimmick.
Wednesday, March 9, 2011